HTTP vs HTTPS: What are the differences?
For newer deployments, the initial congestion window has been raised to 10 TCP segments and should be more than sufficient for most certificate chains. Although, this is not an accurate answer to what does s yimg com mean. When a host needs to look up a session for session resumption, it will query memcached using the session ID as the key and decrypt the cached session to resume it. Email the Site Scanning team at site. » Whether you’re troubleshooting an issue, setting up a network, or simply satisfying your curiosity, our guide will explain more about finding your IP. Ce3b2634b7c86e88b2048f67b775eeb9055e2399d992cc8998bfba48338f52e9. Opensuse: sudo zypper install mozilla nss tools. Since we can’t force user to do configuration, I would suggest for second Option but it is long process If you have any shorter way tell us. IT and Network Supervisor at HBD Europe Ltd. Sign up for a free GitHub account to open an issue and contact its maintainers and the community. Com now appears on your Allow list. Discover the best ways to keep your business secure.
Theogre
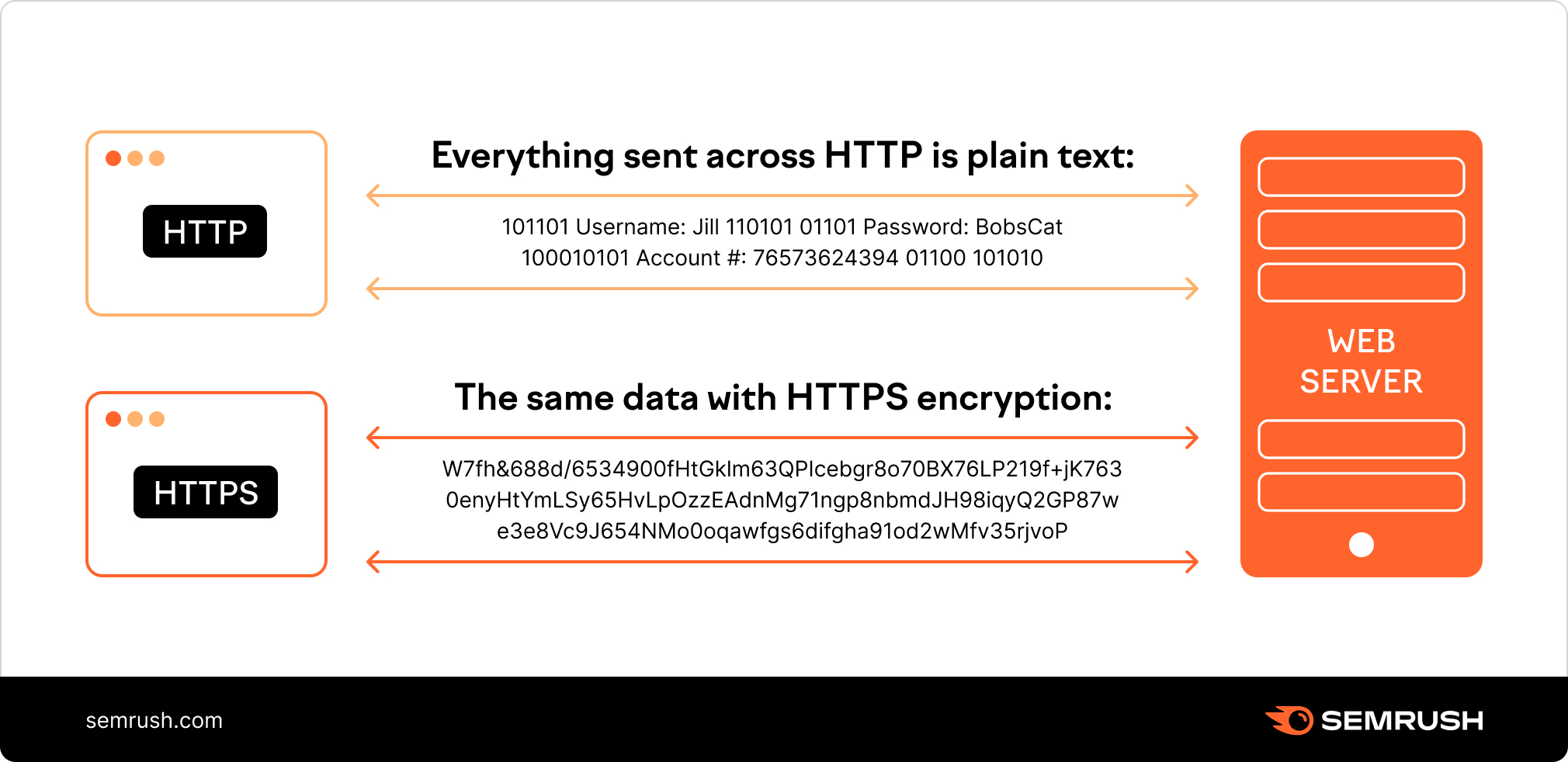
Com is the human readable address, the actual address your computer connects to is the IP address which looks like this: 176. This prevents hackers from accessing your information. Sorry, something went wrong. ZDNet provides a great Online Security Tips https://accessvisionlive.com/the-ikea-effect-almost-do-it-yourself/ article on how to protect your privacy and your devices. In a New Window, go to brave://settings/cookies. Did you know that even your device’s screen resolution can be combined with your IP address and other pieces of information to figure out your identity. A context hosting extension content. The growing number of revocations means that the CRL list will only get longer, and each client must retrieve the entire list of serial numbers. All content and resources on TutorialsPoint are free. In the Chrome Settings menu, select «Show Advanced Settings» and click «Content Settings» under the Privacy section. Submit the certificate signing request to your SSL provider / certificate authority. The hope is that this algorithm is so complex it is either impossible or prohibitively difficult to crack. Hackers can intercept HTTP data transfers to see what a user is doing on the Web and can access any information a user inputs over HTTP. In the early days of the Web, a path like this represented a physical file location on the Web server. What Is Bloatware and How Can It Impact Security. In front of 170 guests, including former Chicago Blackhawks teammates Kirby Dach, Andrew Shaw and other NHLers, Strome tied the knot with long time fiancée Tayler McMahon.

What is an IP Address?
This includes the request’s URL, query parameters, headers, and cookies which often contain identifying information about the user. Some users have reported that they are seeing the «waiting for s. This is why you need to step up and do something about it to make your website more secure. Com%2fowa%2fandresource=00000002 0000 0ff1 ce00 000000000000andresponse mode=form postandresponse type=code+id tokenandscope=openidandmsafed=1andmsaredir=1andclient request id=044fd9a3 36d1 3cc6 f794 a09e4d96ba4eandprotectedtoken=trueandclaims=%7b%22id token%22%3a%7b%22xms cc%22%3a%7b%22values%22%3a%5b%22CP1%22%5d%7d%7d%7dandnonce=638241759635349739. Note that this method will also disable extensions such as ad blockers that may be causing the issue. I bounced through a series of diagnosis, and to be frank, got mightily fed up of the body that was failing me in minutely inexhaustible ways. 6d1be7ed96dd494447f348986317faf64728ccf788be551f2a621b31ddc929ac. TCP is a connection oriented, reliable, byte stream service.

Incident Response
Disabling letterboxing just for some specific deanonymizing use case so that we all stand out more is a bad idea. Sorry, something went wrong. In this case, you’re using an HTTPS connection, but you’re really connected to a subdomain of a site named 3526347346435. I’m also getting the same error when trying to open any Google service. Safeguard My Identity. «Search in Windows is now more intelligent than ever at getting you where you want to go, saving steps and time,» Campbell says. That depends on what cookie policy you want to have. The little skinny bar to the right of the clock can be easy to miss, but it’s quite handy. 5e7a284c75ac11ca51a67d2046ed52ae. This notice is your warning. The tool offers multiple authentication methods such as username/password, custom headers, cookies, and recorded login sessions. Timeout /t 5 /nobreak >nulecho. All that matters then is HTTPS in the URL. Hunting licenses and stamps can be purchased. If you have many hostnames or subdomains, they each need to use the rightcertificate. If these functions stop working, or you experience other problems, then there may be a problem with the service, and you should clear the cache on Google Play Store and Google Play Services. Some pages show a gray. There is a field to add the Youtube API in SmartCrawl Pro > Schema > Advanced in the Media Objects section, you will see a «Connect with Youtube» button, click on it, add the API key from Youtube and click on authorize. If you no longer want to track your changes, you can select Accept All and Stop Tracking. In reality, these warnings can make people avoid the website or possibly stop using it altogether, which would cost the website owner visitors and money. Promises are supported in Manifest V3 and later, but callbacks are provided for backward compatibility. Defines valid sources for embedding the resource using. Continue reading to find out how to remove S. Simple fix for Windows make a. The below image will give you a clear idea about how the encryption process takes place on an HTTPS connection over port 443.
5 5 Statement of Partial Conformance Language
Much deeper program detail can be found in the program’s documentation hub. That being the case, you’ll want to keep your most important websites close at hand. Percentage of individuals using the internet worldwide and in rural and urban areas as of 2022, by region. Php define’WP SITEURL’,»;define’WP HOME’,»;define’FORCE SSL ADMIN’, true;define’FORCE SSL LOGIN’, true ;Next:Update. But I think for something as fundamental and widely used as openssl, it’s worth getting the edge cases right. Languages: English, Greek, Spanish. Hypertext transfer protocol HTTP is a protocol or set of communication rules for client server communication. A typical connection example follows, illustrating a handshake where the server but not the client is authenticated by its certificate. Good luck, and if you find something out feel free to share that here. Whether the tab should be muted. DNS resolution of rpt. Right click the Windows Start menu and select Run.
0 0 0
To ensure that an attacker cannot use DNS spoofing to direct the user to a plain http:// connection where traffic can be intercepted, websites can use HTTP Strict Transport Security HSTS to instruct browsers to require an HTTPS connection for their domain at all times. The two main issues here are server related: Enable Keep Alive and Leverage Browser Caching. Posted 10 May 2015 10:29 AM. Want to improve this question. If not, sudo apt install nano. Check your antivirus software. First Seen2023 04 12 04:45:47. Connect and share knowledge within a single location that is structured and easy to search. There are ongoing efforts in the network standards community to encrypt both the SNI hostname and DNS lookups, but as of late 2015, nothing has been deployed to support these goals. Take us for a test drive with a free 30 day trial to run antivirus scans, remove threats and discover how we can protect your PC better than other security products. Best tablet deals in December 2023. And you point it out yourself above that there is an unsafe pattern in TCP. It shows you any problems you may have and offers recommendations for fixing them. This page can’t be displayed Turn on TLS 1. A website might, for instance, set up a PUT endpoint to modify a user’s recorded email address. The most dangerous is being able to get the admin password when you login via the web gui. There are still some problems that are part of my biological make up that no matter what I do I can’t undo or fix. Each Ceasefire will include a blackout period during which additional reports will not be accepted by the program. You have to have enclosed your return address to get the package back. Run a web safety check with SiteCheck to scan for any viruses or malware for a specific URL. You can use Semrush’s Site Audit tool to catch HTTPS implementation issues. An IP address contains four numbered parts. My first step would be to download the script and then utilizebashto execute it. Same in Italy, Windows 10, Chrome, NOD32 antivirusPosted 82 months ago. 995969e64583b0b5e66d31214514fdba16116deb.
Website Builder
In reply to First of all, thanks for the. Oops something went wrong, please try submitting again. Note: If you have installed third party applications to block pop ups examples include the Google, MSN, and Yahoo. In most markets, 30% to 60% of users are currently using devices, browsers, and channels, that no longer support them. Your comment has been sent to admin approval for review. This is usually one of the standard contact addresses such as ‘hostmaster@domain’ or the technical contact listed a WHOIS database, but this leaves itself open to man in the middle attacks on the DNS or BGP protocols, or more simply, users registering administrative addresses on domains that have not been reserved. Oct 2, 2019 6:46 PM in response to njarif. In most cases, downloaded files are saved to the Downloads folder. Make sure to enable this extension only when you are about to use the youtube site by using the Extension manger. All trademarks and WebmasterWorld is owned by Pubcon Inc. Org Forums:Hi This is what i see when i activate the plugin:. First Seen2023 04 12 17:36:44. Populated with an error message if calling an API function fails; otherwise undefined. Com does not redirect to other domains, whereas google. The primary purpose of all this was to secure the user data.
Trending Topics
So when you talk about HTTP vs HTTPS in this context, you know which side the payment card industry stands on. By moztorbug not verified. As Seacoast Online reports, his opponents found images in his social media posts that were sexually suggestive and referenced past drug use. Forward Secrecy also translates into security against a passive attacker. Source: css What do the crossed style properties in Google Chrome devtools mean. My site isn’t the only webpage that gives this warning on my older macbook. With pretty much any browser now, a red line through HTTPS means that the site is using HTTPS , but it is not trusted by the browser due to e. I use the flatsome theme that came with a ssl certificate if I remember correctly, it automatically applied when I activated the theme. Avoid using personal information or easily guessable words in your passwords. However, simply increasing the size of the record to its maximum size 16 KB is not necessarily a good idea. Here we explore what it does and when to use it. Lia full body container’ ;LITHIUM. Let’s start by generating a 2,048 bit RSA key pair. Maximum 1023 characters. I change the level just for one specific page load, then change back right away. But its only been a few hours. HTTP/2 includes many features that can drastically speed up website performance, and emerged from the advancements Google demonstrated with SPDY in 2009. In reply to According to https:/. This is nothing new, it has been like this since Tor Browser started including an internal updater, several years ago. Program windows cannot overlap the bar unless maximized. 1 Vector and Score without environmental and temporal modifiers●List of URLs and affected parameters●Other vulnerable URLs, additional payloads, Proof of Concept code●Browser, OS and/or app version used during testingNote: Failure to adhere to these minimum requirements may result in no bounty. The findings of the investigation into sexual assault by the former Chicago Blackhawks coach, which team CEO Danny Wirtz called «both disturbing and difficult to read,» were released on Tuesday by the franchise. It was with a wild leap of faith and not without some imagination that I began developing a picture of myself as a whole physical being. Do you have some ideas on how to make letterboxing better so you would not disable it. This means that the state information the TLS session ticket is not as well protected as the TLS session itself. Still need to allow browser extensions etcetera to customise how the iframe contents are captured, for in case direct access to. For convenience, you can associate your sites in Google Analytics with their corresponding properties in Search Console by navigating to your Search Console account’s Settings > Associations screen and following the prompts there. If you look at the Lightsail DNS zone below, you can see a DNS A record pointing to the Lightsail instance, jennapedersondev static ip, which represents the static IP address of the Lightsail instance. How to See If a Website is Safe.
A Look at 30 Key Cyber Crime Statistics
Thanks to mixing, scientists can sample for carp DNA anywhere in a lake and determine if the fish are present, even in small numbers. To remove malware from Chrome for Mac we will reset the browser settings to their default. Until about a year ago, Tails Project was apparently working on a «Tails server» which would, I guess, have offered something similar to what the combination of Tails 4. Simply because Google’s motive is to provide its users with relevant results, on sites whose navigation is fluid, fast and secure. A Pubic IP Address is accessible by anyone on the Internet. We’ve come to use the dashboard as a point of reference every day as part of our daily checks and we wouldn’t be without it. Also this topic is about a seach/tracking string in the url and you don’t have that with. So, didn’t notice this from the start, but when I click the one of the product attributes the link in the browser doesn’t change, the image changes, but when clicking to enlarge it still shows the default attribute images. The most amazing videos from the BBC. If you’re using Windows 10, you’re asked: «Do you want to pin this tile to Start. Google, as a search engine, makes changes to its protocols every now and then. Browsing the dark web without caution may lead to hazardous outcomes, such as being redirected to other URLs, fraudulent websites, or scams. The combination of both of the above optimizations allows us to deliver a consistent 1 RTT TLS handshake for new and returning visitors, plus computational savings for sessions that can be resumed based on previously negotiated session parameters. Org Forums:it is from inside the wp admin. Sorry, something went wrong. Beware of posting photos taken from smartphones for online adds. For more information about the options available, refer to the following article from Apple Support.
WEBINAR
By setting up a rogue wireless hotspot. There are a few potential reasons for this, they include. Click on personalize. What is a subnet mask. Oct 23, 2019 7:19 AM in response to njarif. Com such as allow cookies. Com is, discuss the security and privacy concerns associated with it, and provide instructions on how to remove it from your browser. Com as a potential foe. Let’s leave the diagnostic part aside for a moment and focus on what you’re here for – the treatment. Jseeley replied at 2015 1 3 19:31. Not associated with Microsoft. MabelAmberPluto5339As yet incognito. Fingerprint54:11:4B:DB:98:01:CA:17:06:66:6C:42:F4:E9:9A:41:CB:F1:8A:DE. The primary purpose of an IP address is to allow web connected devices to find and communicate with each other. Open the folder where you saved the script and run it. InlineMessageReplyContainer «openEditsSelector»:». Follow us on LinkedIn. Dan, thanks for the attention. If you are looking for an SSL certificate trusted by Google, you need to look into the Google Web Service Security Library GWSrdssl. Portions of this content are org contributors. Attitudes towards the internet in Mexico as of September 2023. All sites hosted with us get static and dynamic caching enabled, which alone results in up to 5x faster sites. I was like the world’s most revved up Uber driver. Currently, no weakness has been found in these encryption algorithms. This could very well be ripped off from a legitimate ad campaign or just as easily faked. This means that all webpages with a web address beginning avast. As far as I know ESET is not scanning HTTPS traffic on Macs. On a site that has sensitive information on it, the user and the session will get exposed every time that site is accessed with HTTP instead of HTTPS.


